The Big Idea for Zapier: Contextual 2FA Promotion
March 2018 is Zapier month! Our Big Idea for Zapier is contextual 2FA promotion: an even better way to encourage users to enable two factor authentication!
Welcome back to Zapier month here at All Things Auth!
This series includes all of the fun details that we gathered during our review of Zapier that we didn’t have nearly enough time to talk about during the Zapier screencast episode.
Each month, we come up with one Big Idea that we think will have the biggest impact for the featured service provider.
Our Big Idea for Zapier this month is contextual 2FA promotion: an even better way to encourage users to enable two factor authentication!
To the talented folks at Zapier: if you only take one thing away from All Things Auth this month, we think it should be contextual messaging for 2FA!
Keep in mind that we don’t have insight into or intimate knowledge of Zapier’s service and user base, so this advice aims to present a general concept and not necessarily specific implementation guidance. We don’t know who Zapier’s target audience is, what their tech stack is comprised of, which business metrics are important to them, nor a history of things they may have tried in the past. Nonetheless, our goal is to improve security through education, thoughtful user experience, and technical best practices and I think that this Big Idea will help steer Zapier in a direction that makes their users more secure.
How Zapier currently promotes 2FA
Another article in this series does a deep dive on Zapier 2FA and how their implementation currently works, but let’s set the stage by reviewing a few key points here.
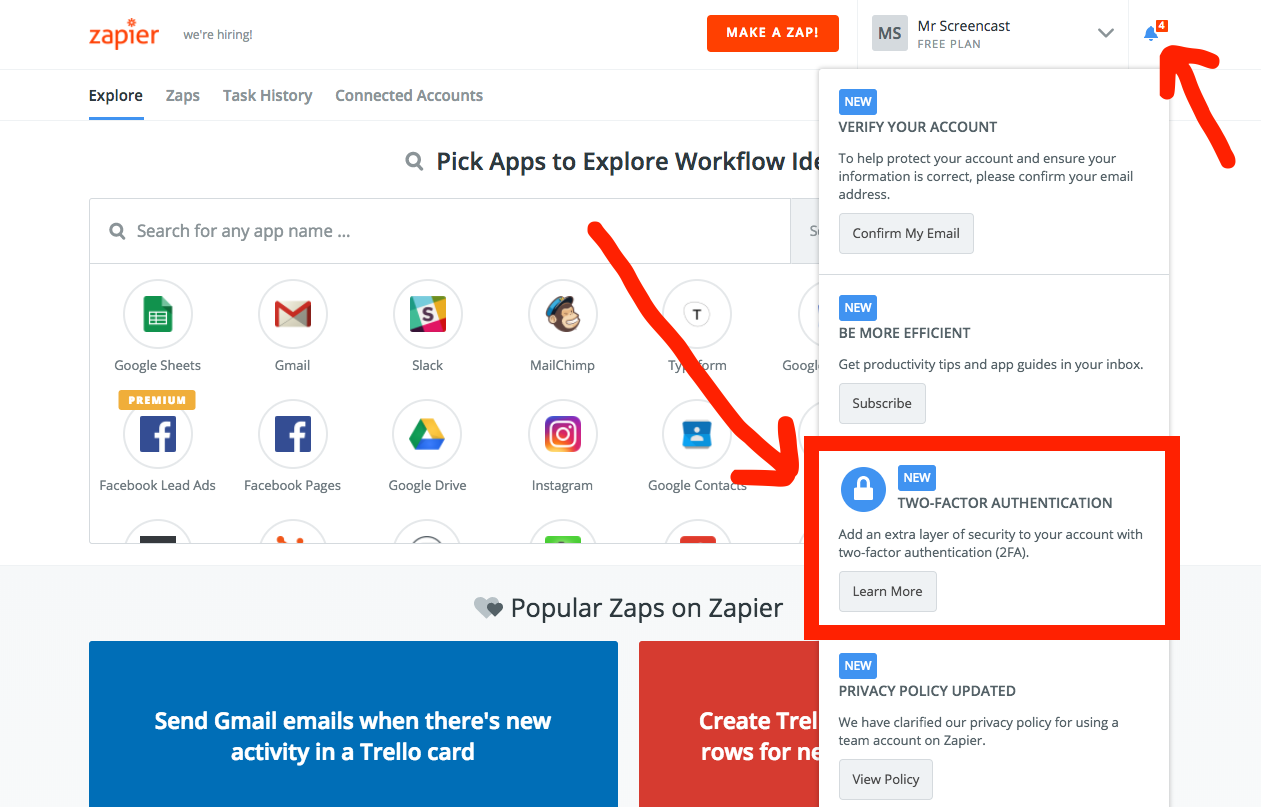
As you can see in the screenshot above, the bell icon in the top right corner prompts new users to take a few actions after creating their account. One of the notifications specifically asks users to enable 2FA. This is a much more proactive approach than many other services take when it comes to 2FA!
However, I think that Zapier can do an even better job encouraging users to enable 2FA and that is where the Big Idea comes in.
Promote 2FA when users have something worth protecting
Instead of just promoting 2FA a single time in the notification menu, 2FA could be promoted contextually depending on their interaction with the Zapier service. Contextual messaging can be applied in a variety of ways. I think that the two most effective scenarios to promote 2FA would be:
- after a certain engagement metric is met; and
- after a Zap is created for a sensitive app, like Quickbooks.
After X Zaps, promote 2FA!
If an account doesn’t have any Zaps created, then there isn’t really anything to protect. As users create Zaps, Zapier becomes more valuable to them. At a certain point, they will hit a critical number of Zaps that is likely worth protecting. It’s at this point that a user would be most receptive to a 2FA suggestion. What was once potentially a cognitive load, is now a helpful tip.
While I suggest using the volume of Zaps as a trigger, there might be a more appropriate metric by which to measure engagement levels, such as the volume of data flowing through a single zap, or which specific third party integrations are used in Zaps.
The promotion should be contextual to where users might be. One option is to display a banner on the first page where users land after logging in.

In this example, I sketched out a potential solution where the promotion is front and center, not hidden within the notification menu in the top right. This helps to give the suggestion to enable 2FA much more visibility. The text and imagery could also be contextual to the specific Zaps that the user has created.
For example, the Twitter integration actions which allow you to create and post new tweets. The 2FA promotion could be displayed with the Twitter icon and a contextual message:
The Twitter integration allows you to create and post new tweets! Enabling 2FA is a great way to add an additional layer of security to your account to make sure that you are the only one who can access your account. One malicious tweet could damage your company’s reputation!
The banner modal also contains a “No Thanks” button, which allows the user to dismiss the 2FA promotion if they can’t or don’t want to deal with it right now. If the user does take this route, then the banner promotion shouldn’t be shown again in the same way for some period of time. How long and in what context this appears is a question that Zapier is most qualified to answer, but it is a good idea to periodically remind the user that enabling 2FA is important while respecting their request to not be bothered. One potential context to bring up subsequent 2FA promotions might be when other services experience a data breach. If there is enough media coverage, users might be more receptive to added security suggestions or even learning more about how to better protect themselves (like not reusing passwords and creating stronger passwords).
In addition to a banner on the homepage, another option is to send the user an email notification with a contextual message encouraging them to enable 2FA.
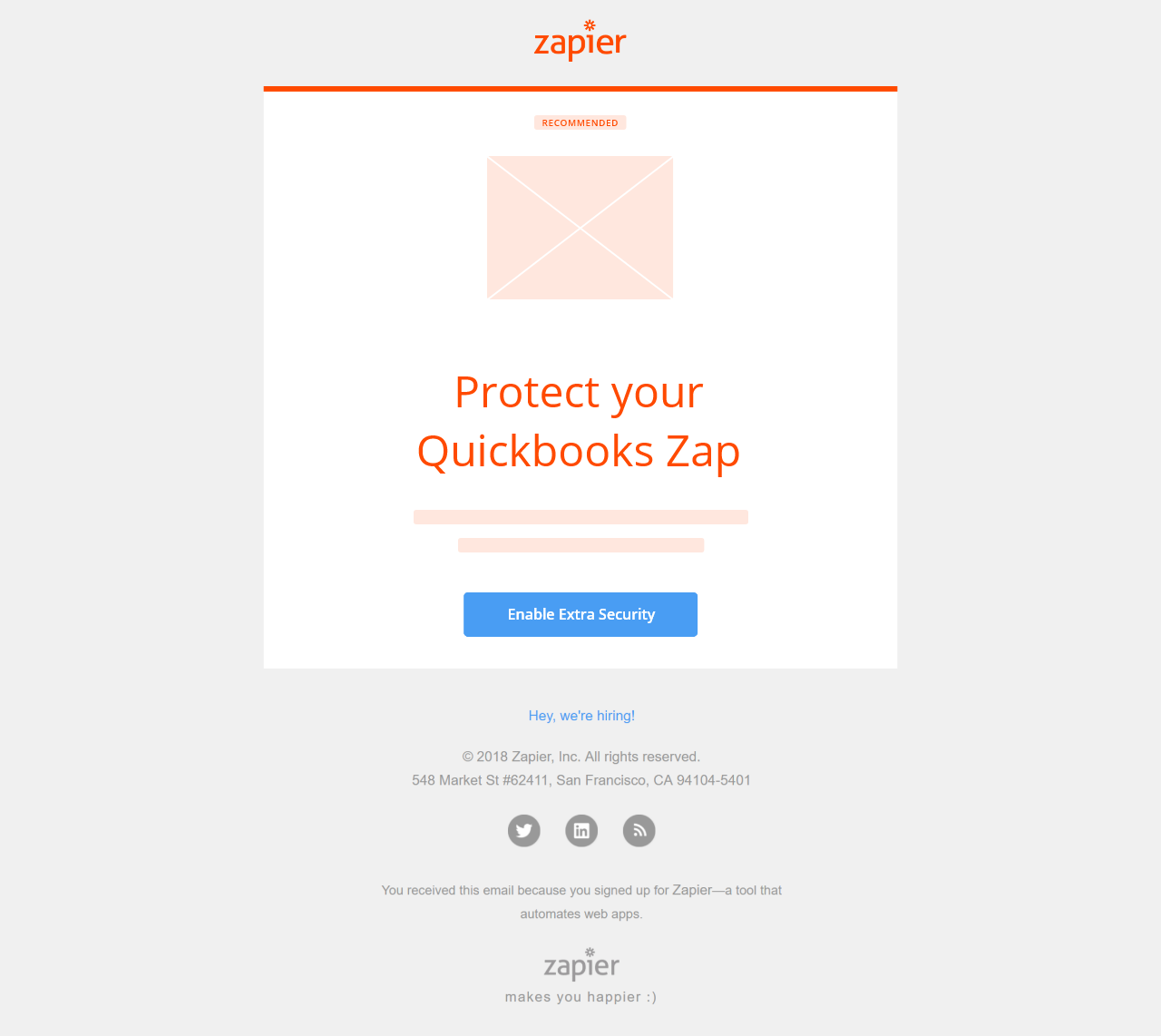
After a Zap is created, a user may not need to visit the website again unless they need to make a change to an existing Zap. As such, they may only engage with Zapier through email notifications. By sending a 2FA promotion through email once the engagement metric is met, we intercept the users exactly where they expect to hear from Zapier: their inbox.
Promote 2FA on creation of “sensitive” Zaps
The idea here is very similar, except that the 2FA promotional message is contextual to a specific Zap.
Certain applications are inherently sensitive. Integrations that deal with finances, like Quickbooks, fall into this category. If someone were able to access your account using a compromised password, a Zap with Quickbooks might be incredibly damaging to your business.
Therefore, once a Zap with such an app is created, users may be much more motivated to protect Zaps with potentially sensitive data. It’s in this context that I suggest promoting 2FA.
For example, the Quickbooks integration has triggers to let you know when a client pays you money and actions which allow you to create and send invoices to request clients pay you money. If the user has integrated with Quickbooks, then the 2FA promotion could be displayed with the Quickbooks icon and a contextual message:
Quickbooks can send invoices to your clients! Enabling 2FA is a great way to add an additional layer of security to your account to make sure that any invoices that get sent to your clients aren’t modified by someone who has stolen your password and gotten into your account!
The most appropriate place might be at the end of the workflow for creating a Zap with a sensitive third party service. The sketch below suggests making an optional final “step” where users can enable 2FA. It would explain why this is a good idea when this type of Zap is created.
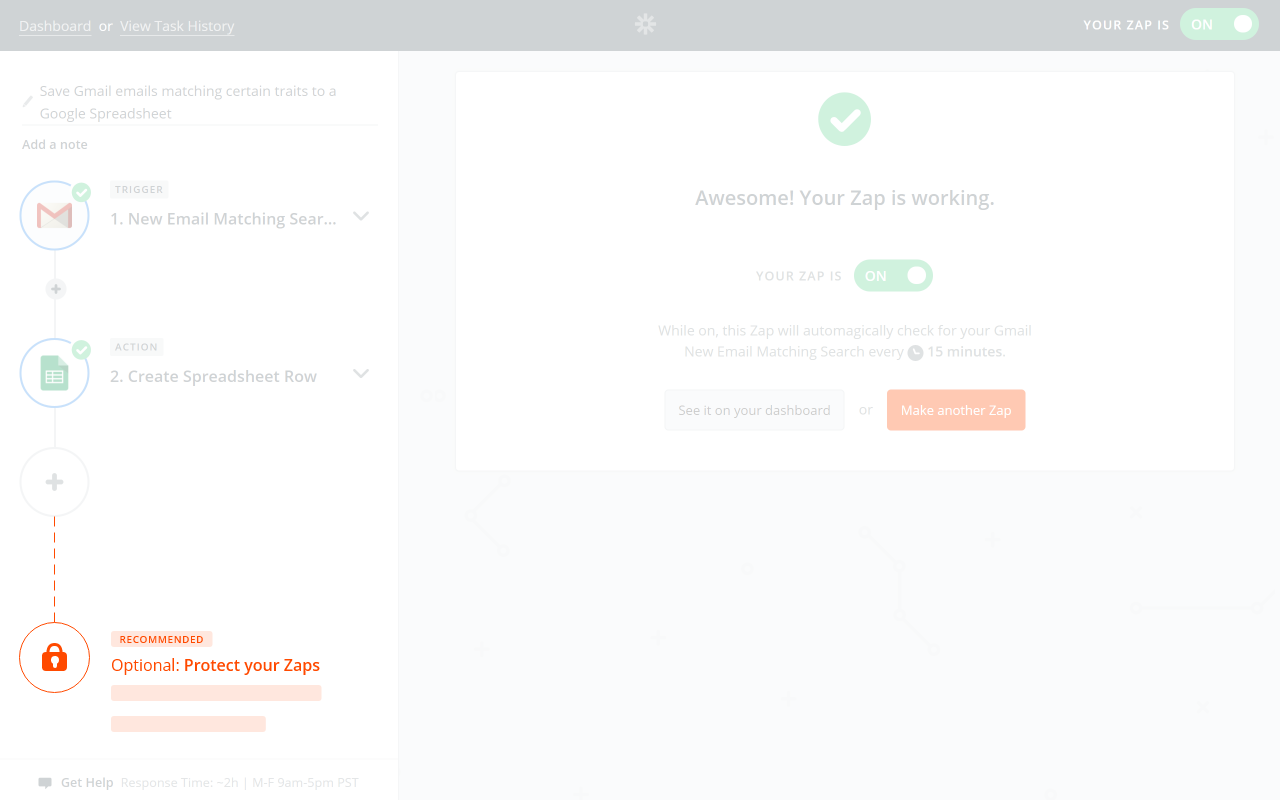
I also considered placing this promotion under the final success message itself. The potential risk is that users may have formed a habit with the “See it on your Dashboard” and “Make another Zap” buttons. They may accidently click on the “Enable 2FA” button, causing frustration rather than encouraging users to enable 2FA.
It is critical that any implementation presents the suggestion to enable 2FA in a way that users find helpful and not an annoying hurdle.
How can Zapier tell whether contextual 2FA promotion provides value?
Improving security is like IT work. No one really appreciates it until something is broken. User security shouldn't be an afterthought that is added on just to say you have it. It should be deliberate. All interactions should be considered with the user's best intentions in mind. Otherwise, the risk is alienating your users through apathy.
I also believe that if you want your users to love you (or your service), you should love them back beyond just a monetary level. In my opinion, Zapier certainly loves their users. This is evident by their thoughtful approach to user experience. But even so, it’s not always easy to know how much value a security feature is providing.
Here are a few ideas on how Zapier might measure the value of contextual 2FA promotion.
First, they can perform an audit on the strength of users’ existing passwords. If many users have weak passwords, then a second authentication factor will help mitigate unauthorized account access. This would be evidence to help support efforts to get users to enable 2FA.
In addition, they could compare the metrics of unauthorized account access incidents between users who do have 2FA enabled and users who do not have 2FA enabled. As Zapier encourages users to enable 2FA, I would expect 2FA adoption rates to increase and unauthorized access incidents to decrease.
It might be a reasonable assumption that an average user would reach out to Zapier support if they tried to log into their account and their password had stopped working without them resetting it. The user might ask support what is going on and which steps they should take to reset their password and regain control of their account. An increase in 2FA adoption rate should also reduce the support burden caused by unauthorized account access incidents by preventing unauthorized access in the first place.
Finally, the contextual 2FA promotion could simply be a better user experience that users appreciate. An increase in Net Promoter Score (NPS) might indicate that it is well received by users, but your mileage may vary.
Potential pitfalls for contextual 2FA promotion
With any new feature or function, there are always pitfalls. Some can be avoided with some forethought, others are unknown until you encounter them.
Here are a few pitfalls that I can foresee:
Contextual messages could become annoying if poorly implemented
Notifications should appear when desired but otherwise stay hidden. To receive a notification out of context would be like getting a telemarketing call right at dinner time. Nobody wants it, and in fact will hate you for it. If these contextual 2FA promotions are implemented, then they should only appear when necessary and useful for users.
Contextual messages could still be ignored
Currently, the only 2FA method that Zapier supports is Time-based One Time Password (TOTP). This is great from a security point of view, but many users might not be familiar with TOTP and instead familiar with the ubiquitous and less secure SMS 2FA. This lack of familiarity might make users hesitant to enable a method of 2FA that they are not familiar with. To help mitigate this, smart education and guidance should be introduced to the user. This could potentially take the form of how-to videos, educational campaigns as to why SMS is not an option, etc. In this case, some research and testing should be done to find just the right balance of guidance, education, and contextual notification.
Contextual messages could actually increase support burden
Counterintuitively, increased 2FA adoption rates could cause more of a support burden depending on certain aspects of the existing 2FA implementation.
TOTP 2FA requires users to download and save recovery codes in case they lose access to their phone. As discussed in the Zapier 2FA Deep Dive article, we think that Zapier’s current messaging on the topic does a great job of warning users not to lose their recovery codes. However, we are likely more technical than the average user. People who do end up losing both their phone and their recovery codes will likely reach out to Zapier support even though it is clearly communicated that support will not be able to help recover the account in that scenario. Zapier should run tests to make sure that their users fully understand what they are getting into so as to mitigate issues where users don’t pay attention to what they are doing and end up in a sad place.
Conclusion
Zapier already does a bunch of things very well. They are incredibly thoughtful about their user experience and have a great 2FA implementation. With our surface level knowledge of Zapier, we feel that the best way to improve Zapier user security would be to encourage more of their users to adopt 2FA.
Our runner up Big Idea is to encourage users to create stronger passwords. However, it is incredibly difficult to change user behavior when it comes to password hygiene and we would still recommend enabling 2FA on top of that. Check out the Two Factor Authentication series for some great background on why even users with strong, unique passwords should enable 2FA.
Don’t forget that all of March is Zapier month! Join the email list below to make sure you don’t miss the rest of this series. There will be an article focusing entirely on how Zapier deals with passwords!
Lawery disclaimer: All Things Auth is not associated with Zapier in any way. We decided on our own to write this article because we like Zapier. All views expressed here are those of the author based on use of the public Zapier service only.
Thanks to Conor Gilsenan for reading drafts of this.