How Zapier rolled out 2FA support
Two factor authentication (2FA) doesn't provide effective security if users don't enable it. Learn how Zapier announced the rollout of 2FA to its users!
Welcome back to Zapier month here at All Things Auth!
This series includes all of the fun details that we gathered during our review of Zapier that we didn’t have nearly enough time to talk about during the Zapier screencast episode.
In this article, we are going to take a look at how Zapier announced support of two factor authentication (2FA) to its users.
Let’s get into it!
Communication is a critical part of security UX
As I discussed in Security features are features too!, there is much more to implementing a security feature than just writing code.
All aspects of the user experience (UX) must be considered first class priorities for any feature that hopes to provide effective security.
After the technical implementation is in place, it is critical to tell users that the feature now exists and convince them to actually enable it.
One of the most obvious ways to announce a feature is to steer users towards it via the user experience of the product itself. Previously in this series, we talked in depth about how Zapier promotes 2FA on the website. However, Ray also highlighted in his post that many Zapier users may not interact with the website on a regular basis. I have certainly found this to be true in my personal experience. After I created a Zap to automate my workflow, I had no need to visit the Zapier website again unless I needed to make a change.
The best way to reach Zapier users is likely via email.
The 2FA email announcement
Zapier announced support for 2FA in their March 2017 newsletter.
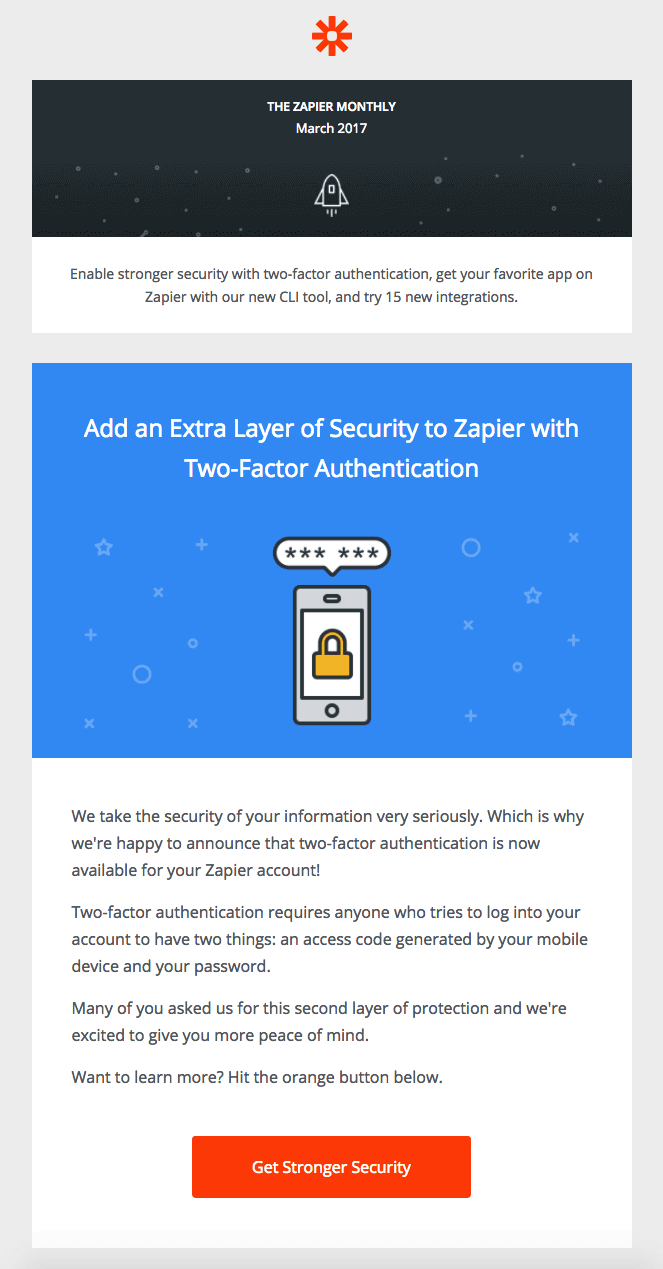
It is great that Zapier proactively notified users about 2FA support and encouraged them to enable it. I really like that 2FA was the first topic addressed in the email and that the CTA button text was strong: “Get Stronger Security”. However, there are many ways that the initial email announcement could have had more impact.
This 2FA announcement was included in the March 2017 newsletter, which makes sense considering it was an important update in the Zapier community. However, it is possible for users to easily opt-out of receiving these newsletters.
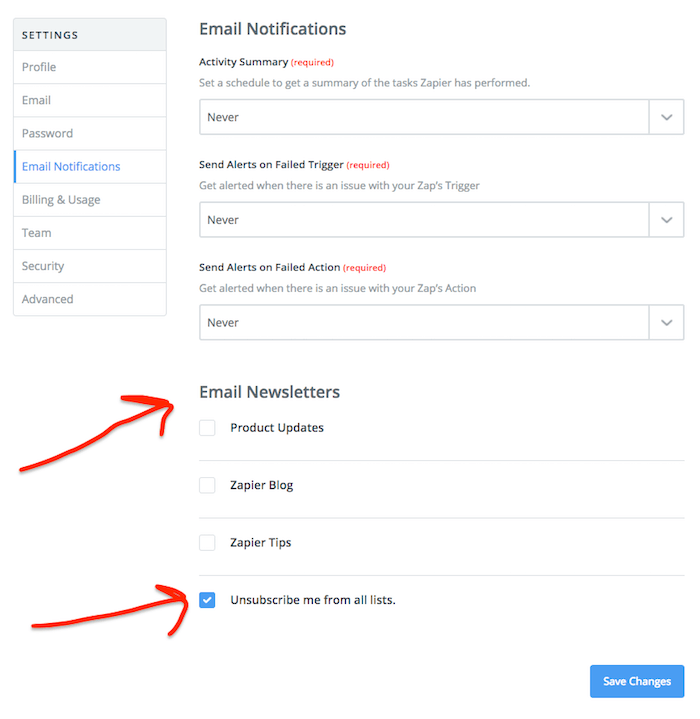
It is likely that existing Zapier users who unsubscribed from marketing emails did not receive this announcement email. Those users’ accounts remained at a lower level of security until they next logged into their account and noticed that 2FA was supported. That could have been days, weeks, or even longer assuming they didn’t have to make a change to a Zap or create a new one.
❗ Improvement: Zapier could have treated 2FA support as an important security notification and sent an email to all existing Zapier users.
The other issue with announcing 2FA support in the monthly newsletter is that it is mixed in with tons of other content that could distract the user from the important security call to action. The screenshot above was intentionally cropped to only show the first section of the newsletter.
The subject of the email was “Get Two-Factor Authentication, Try 15 New Apps, and More” and highlighted powerful new developer tools:
And also announced 15 new Apps and 23 new Integrations:
And wrapped up by summarizing some of the most popular posts and guides from the past month:
(You can see the email in its entirety over at Really Good Emails here.)
I can easily see a user reading the important security information about 2FA, getting distracted by the rest of the content in the email, and forgetting to circle back to actually enable 2FA.
❗Improvement: The email announcing 2FA support should have been security specific and not contained unrelated information. Limiting the email to a single topic reduces the chance for distraction or dismissal.
The 2FA blog announcement
The “Get Stronger Security” button in the newsletter links to a blog post with additional information about 2FA support on Zapier. This blost post is well written and does a better job of explaining what 2FA is than the teaser text in the announcement email. There are some key phrases that I find particularly effective:
Enabling two-factor authentication isn't required to use Zapier—but we highly recommend it. Being proactive about your account's security is the best way to keep the bad guys out.
Now, I hear you saying, “I use a long and random password for my account.” And that's good! But passwords only represent a single piece of information someone needs in order to access your account. If someone gets their hands on your password, they've got the keys to your automation kingdom.
(emphasis mine)
I have written about many of the ways that even a strong and unique password can be compromised. It is great to see Zapier address that specific point too, but the most important sentence in that entire blog post might be that one I emphasized. It would have been great if the author went even further and provided some specific examples of what someone could do with unauthorized access to your account: rogue tweets, false invoices, etc.
⭐ Excellent: The author makes it clear that 2FA can help protect “the keys to your automation kingdom”.
The blog post wraps up by linking to a companion post with more technical details about how 2FA works, why it is important and how to enable it for Zapier and several other popular services. Also, there is a link to the Zapier 2FA help docs, which I think are very well presented. I’ll cover the help docs specifically in an article later in this series. Stay tuned!
The 2FA social media announcements
In October 2016, Zapier responded to a customer request for 2FA support by saying that it was on their roadmap. They followed through 6 months later and tweeted New Feature: 2FA in April 2017.
NEW FEATURE: Upgrade your account security by enabling two-factor authentication (2FA). Now available in Zapier! https://t.co/LJU097Z3pJ pic.twitter.com/w6OZSRv9bQ
— Zapier (@zapier) April 4, 2017
This tweet only has 1 comment, 0 retweets, and 7 likes; of those 7 people who like it, at least 3 actually work at Zapier! Of course, there is nothing wrong with liking your own tweets, but those response rates are quite low if the goal is to inform your users about a critical new security feature.
A second tweet on the same day (You asked! We listened!) only managed to snag 1 comment, 3 retweets, 3 likes. Even if these tweets had reached a large portion of the Zapier user base, there are many users who simply don’t use Twitter.
Zapier also announced 2FA on Facebook with similarly lackluster results. Their initial post only garnered 4 likes and 1 share. A follow up post about the importance of 2FA received only 1 like and 1 share.
Zapier should be commended for posting a reminder about the importance of 2FA in August 2017, five months after initial rollout, in response to a large data breach:
The latest huge data breach (711 million emails) is a good reminder to make sure you have two-factor authentication turned on:
Posted by Zapier on Thursday, August 31, 2017
They don’t mention which breach they are talking about, but the post was likely a reaction to the Onliner Spambot breach that compromised 711 million user records. Communication is a critical part of security UX and that doesn’t just stop after initial rollout. Regular communication and reminders are always helpful and even better when they are contextual to a specific data breach that has increased the risk to Zapier’s users, like in this case. Sadly, the post didn’t get any reaction to speak of, but that is certainly not a reason to stop this type of useful communication!
In summary, a valiant effort by Zapier to leverage their social media accounts to announce 2FA support, but those channels do not appear to have been very effective for reaching the majority of Zapier end-users.
[IMPORTANT] Don’t lose access to your account
In late 2017, around the holidays, Zapier sent out an email with that eye catching subject:
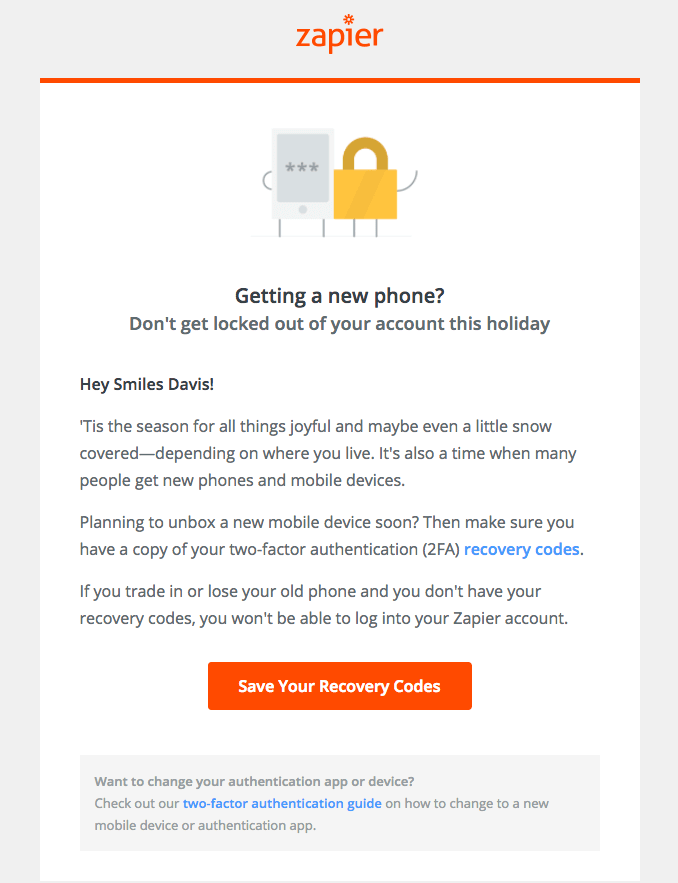
My first reaction upon discovering this email was: “Wow! This is awesome!”
⭐ Excellent: I have never seen a service proactively email their users regarding 2FA like Zapier did with this email. It makes so much sense that I can’t believe that more companies don’t do it.
The summary of the email over on Really Good Emails provides some context:
Timely email Zapier just sent out after noticing a huge spike in people getting locked out of their accounts because they got new phones for Black Friday.
Assuming that is accurate, it seems that Zapier wasn’t entirely proactive. Instead, they realized that users were accidentally locking themselves out of their accounts because they didn’t have their recovery codes saved before they got a new phone over the holidays.
Regardless, this email is still awesome and is a great attempt to address the situation once the problem was discovered. I would love to see Zapier continue to do this on a regular basis. They could send this recovery code reminder email a few select times per year to users who have 2FA enabled:
- around the holidays when people tend to buy phones as gifts
- before a new phone is released by a market leader, such as Apple or Samsung
I do wonder whether this email actually addressed the spike in accidental account lockouts by increasing recovery code download rates among users. As I discussed in the 2FA deep dive earlier in this series, Zapier made it very clear that if users lose their phone and lose their recovery codes, then they will be permanently locked out of their account.
I also wonder whether users who did get locked out eventually recovered their accounts somehow. Zapier has replied to several users on Twitter telling them to contact support after getting locked out. I wonder if there actually is an undocumented account recovery process...
Based on the timeline, I wouldn’t be surprised if this was the first such spike in account access issues since 2FA was rolled out in April. I am curious whether Zapier made any corresponding changes to the 2FA workflow to highlight the importance of recovery codes. Just like any other “core” feature, security features should improve over time as they incorporate real world feedback from users.
Wrap up
Overall, a mixed bag on announcement of 2FA support.
Zapier does a great job informing new users that 2FA is supported (and they could do an even better job if they used contextual messaging), but the main goal when first rolling it out was to notify all of the existing users. Social media appears to have been largely ineffective and the 2FA announcement in the March 2017 newsletter was likely not received by users who opted out of marketing emails.
It is important to point out that Zapier defaults all users into receiving the marketing emails, so it is possible that most users were included; only Zapier knows the concrete numbers there. It is also possible that Zapier sent out additional 2FA announcement emails that I was not able to track down during my research.
However, I still feel strongly that the most effective strategy would have been to send a security notification email to all users announcing 2FA support and explaining why they should enable it. Stronger wording would also likely have prompted more users to take action. Stealing wording from the 2FA blog post would have been a nice call to action for a security notification email: “If someone gets their hands on your password, they've got the keys to your automation kingdom.”
Finally, the recovery code reminder email showcases how ongoing communication with users can help them get the most out of the security features they are already using. That simple reminder probably helped many users avoid getting locked out of their accounts over the holidays.
If you’ve stuck it out til the end, then you should definitely join the email list below to make sure you don’t miss the rest of the Zapier series this month! We still need to take a look at creating and changing passwords on Zapier and the extremely useful help documentation.
Let Zapier know that you want to hear from them too! Send them a tweet!
Lawery disclaimer: All Things Auth is not associated with Zapier in any way. We decided on our own to write this article because we like Zapier. All views expressed here are those of the author based on use of the public Zapier service only.
Thanks to Jordan Fischer for reading drafts of this.
